OneM2M overview
oneM2M is a global partnership project founded in 2012 and constituted by 8 of the world's leading ICT standards development organizations, notably: ARIB (Japan), ATIS (United States), CCSA (China), ETSI (Europe), TIA (USA), TSDSI (India), TTA (Korea) and TTC (Japan). The goal of the organization is to create a global technical standard for interoperability concerning the architecture, API specifications, security and enrolment solutions for Machine-to-Machine and IoT technologies based on requirements contributed by it’s members.
The produced standardized specifications enables an Eco-System to support a wide range of applications and services such as smart cities, smart grid, connected car, home automation, public safety, and health.
oneM2M technology is removing fragmentation in the IoT world. Because it is independent of the connectivity- or protocol technology that is used for transport, it is designed to be a long term solution for IoT deployment.
Organization
Membership
A oneM2M Member is any legal entity which has an interest in the development and/or implementation of oneM2M Technical Specifications and Technical Reports. oneM2M Members must be members of a oneM2M Partner:
- ARIB – Japan
- ATIS - U.S.
- CCSA – China
- ETSI – Europe
- TIA - U.S.
- TSDSI – India
- TTA - Korea, and
- TTC - Japan.
Members can attend and participate in the oneM2M Technical Plenary and its working groups where they have one vote each. They can also attend the oneM2M Steering Committee meetings but do not have voting rights.
oneM2M currently have more than 200 participating partners and members, among the main actors of the ICT industry like for instance Nokia, AT&T, BT Group, Samsung, Telecom Italia, IBM, Deutsche Telekom, SK Telecom, Cisco, Orange, Qualcomm, InterDigital, Intel, Huawei, LG Uplus, KDDI, etc .... The full list of members may be found here.
For more information on how to join oneM2M please go to the web site at the section Join .
oneM2M actively encourages industry associations and forums with specific application requirements to participate in oneM2M, in order to ensure that the solutions developed support their specific needs.
oneM2M Standard
It is an open standard with a transparent development process & an open access to all deliverables. All the specifications, even the drafts are available at http://onem2m.org/technical/published-drafts
ITU-T Transposition
The oneM2M standards are internationnaly recognized and transposed by ITU-T under the Y.4500 series (see https://www.itu.int/rec/T-REC-Y/en)
Technical Overview
Service Layer for multivendor interoperability
The architecture standardized by oneM2M defines an IoT Service Layer, i.e. a vendor independent software Middleware sitting between processing / communication hardware and IoT applications providing a set of functions commonly needed by IoT applications.
The oneM2M Service Layer provides use case independent functions.
- oneM2M Common Service layer Functions (CSF’s) provide proper:
- Identification of users and applications
- authentication & authorization of users and applications
- end-to-end data encryption
- remote provisioning & service activation
- device management,
- connectivity setup & data transmission scheduling,
- data aggregation, buffering in case of missing connectivity and synchronization upon connectivity re-establishment
- group management and application and data discovery functions
- etc ...
The functions listed above provided by the oneM2M common service layer, are exposed and controlled via globally standardized vendor independent and uniform APIs, towards the IoT applications.
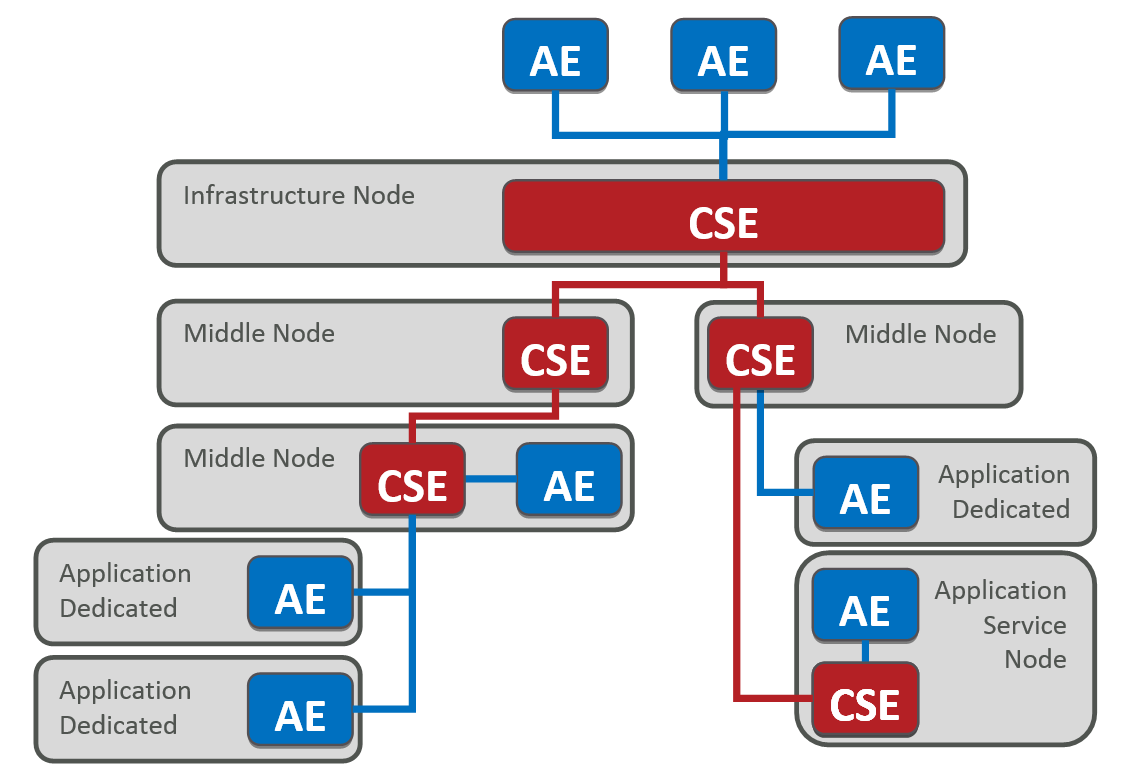
IoT applications or more generically “Application Entities” AE’s are generic terms for applications executed in so called Application Dedicated Nodes ADNs or Middle Nodes MNs and at the Infrastructure Node IN.
Applications (AEs) at the device (ADN, MN) and the Infrastructure Platform (IN) are separated by the oneM2M APIs from the actual oneM2M Common Service functions (CSFs) like the ones listed above.
Details and specifics of the underlying- connectivity technologies, transport protocols and data serialization formats are not exposed to the application developer. This avoids the necessity of detailed expertise in used connectivity technologies, and hence allows the application developer to focus on the customer actual IoT application.
Interactions between oneM2M Common Service functions (CSFs) and the application are solely based on the oneM2M globally standardized, vendor independent, uniform APIs towards the applications.
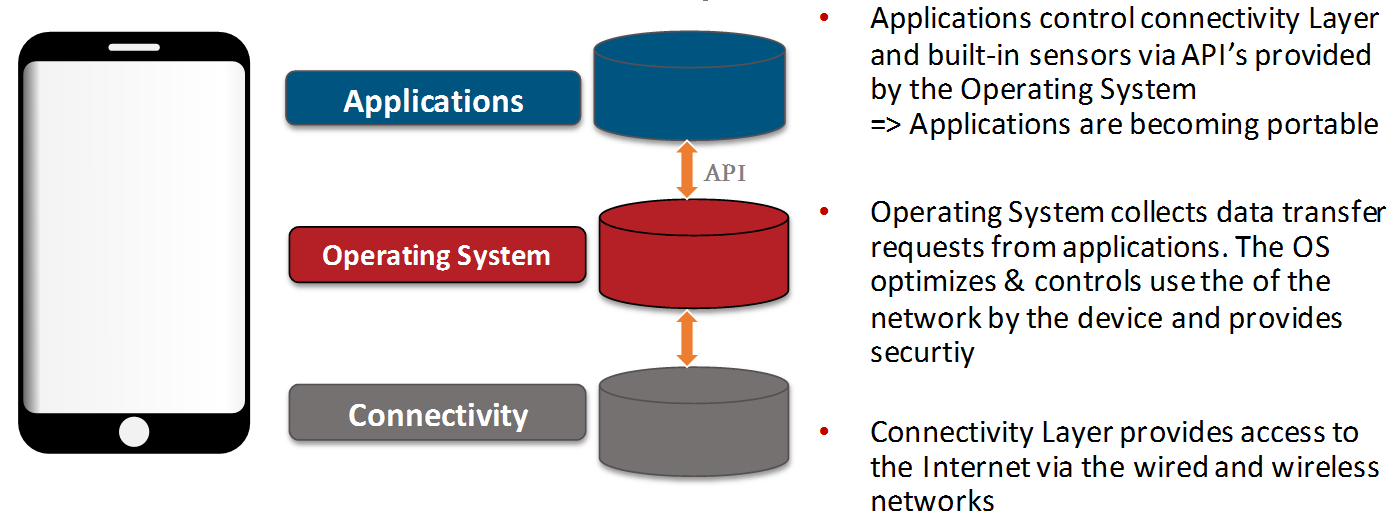
For an application developer, oneM2M based technology appears like an operating system, which takes over common basic functions in context of connectivity and hardware as listed above. Hence the IoT Service Layer specified by oneM2M can be seen in a similar way as a mobile operating systems within the smart phone eco system.
Due to this separation, application developers can focus on the developing the actual IoT application for the Device e.g focusing on:
- Measuring physical parameters, preprocessing of data, controlling attached hardware or Interworking with other technologies (Modbus, CAN-Bus, OPC-UA gateways etc.)
On the infrastructure (Platform) the separation by APIs between oneM2M Common Service functions (CSFs) and application, enables a separation between “low level” tasks in context of connectivity over wide area networks (Device Management, scheduling of data transmission, enrolment of security functions and credentials, revocation of faulty device applications), and actual cloud and IoT application Platform like:
- Data analytics, Rule engines, presentation of data, User interfaces etc.
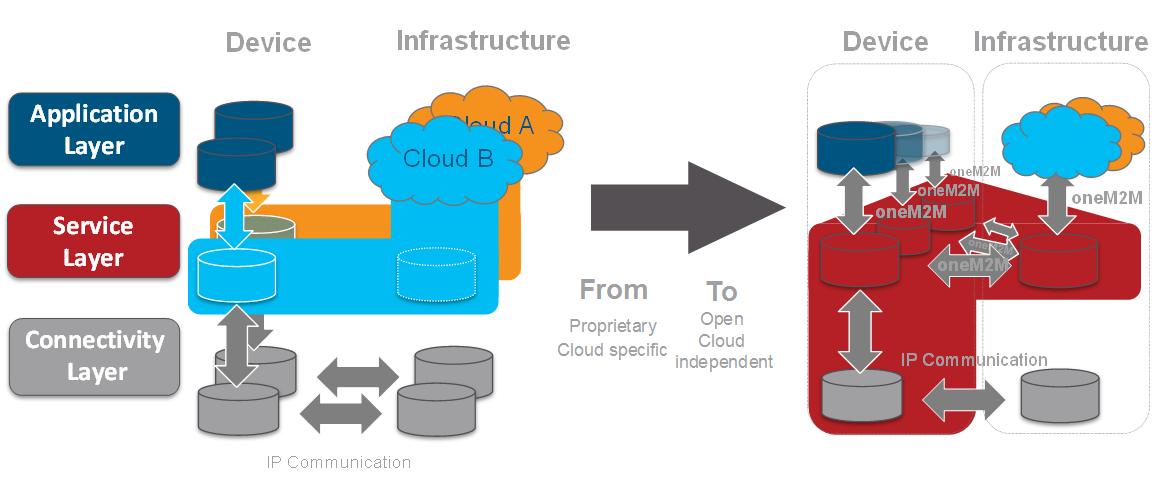
Compared to IoT devices being connected to IoT Platforms without oneM2M, the separation between Applications and oneM2M Common Service functions (CSFs), enables the possibility to become independent form the actual cloud respectively IoT Application Platform provider, since from the viewpoint of the oneM2M Common Service functions (CSFs) the actual cloud respectively IoT application Platform is regarded as an Application (AE) => Bring your own Cloud (BYOC).
Beneficially the oneM2M Common Service functions (CSFs) will become part of the communication chipset, to achieve a coverage in a wide range of devices.
Service Layer for cross vertical interoperability
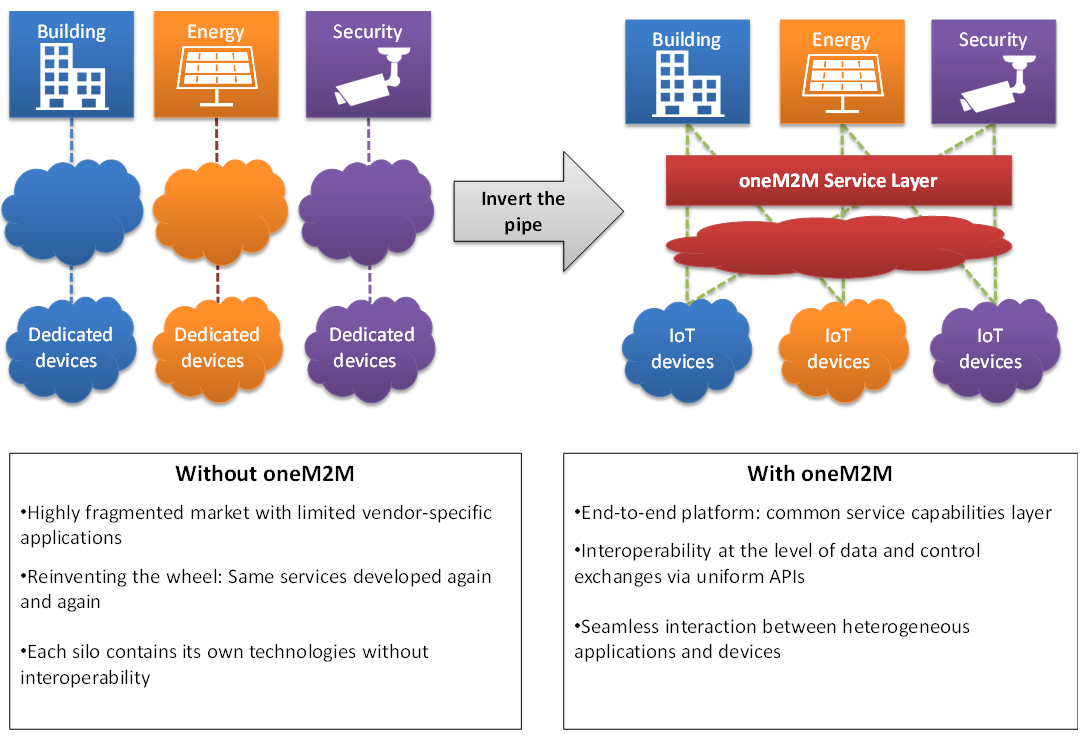
The cross vertical interoperability challenge:
- Before an application executed in car (Automotive) or on a smartphone app is able to open a (Home Domain) garage door (e.g. once a car owner appears at home), both applications need to be properly authenticated and authorized. Moreover both application need to have a common understanding about their specific data models.
- Furthermore if data generated by IoT devices are distributed and uploaded to various different IoT platforms, data are locked in or just accessible within their proprietary IoT platforms. Hence cross vertical use cases are hampered.
In to overcome these aspects oneM2M provides data models based on the so called Smart Device Template which is continuously extended with new functionalities and elements. Basic elements can be modular composed to cover a wide range of devices with various capabilities.
Due to a common understanding of the data being transferred, stored and exposed by the oneM2M Common Service layer via globally standardized, vendor independent, uniform APIs, applications are able to interwork across any vertical.
In order to control access to data generated by IoT devices, oneM2M provides Access Control Policies ACPs, controlling which applications AEs are allowed to access which parts of the data in the oneM2M Common Service layer.
Benefits of using oneM2M
- Easy interworking/integration with existing & evolving deployments paves the way to long term evolution and sustainable economy.
- Does not disrupt existing “vertical deployment”, but evolves it. Supports interworking with legacy technology.
- Interworking with a rich set of proximal IoT technologies, embracing different ecosystems.
- Takes advantage of the operators’ network capabilities and existing management technologies.
- Service Layer on top of transport network supporting a choice of transport protocols and serializations of data/message
- Flexibility: it can be deployed on all domains, not tied to a particular protocol technology.
- IP based: relies on known existing APIs to handle IP communications.
- Aware of optimizations if underlying network is 3GPP-based: can make use of policy-based scheduling, power saving mode, triggering /wakeup of devices, non-IP data transport, etc without the need for the developer to be aware of these terms
- Enhances data sharing efficiency: communications over an underlying network are policed by provisioned policies that govern the use of network resources based on configurable categories of events/messages. Avoids storm of low-value messages in netoworks with costly resources. Lowers Opex.
- For example, in use cases with a need for fast & compact message exchanges one may want to rely on TCP sockets (opened via web sockets) and use binary serialization (e.g. CBOR) whereas in other cases a combination of HTTPS/JSON may be preferable for simpler debugging.
- Evolution: supported transport protocols and/or message serialization can evolve while the oneM2M code will not change. This allows for easy adaptation to future transport technologies.
- Horizontal platform provides common service functions that enable multiple IoT domains
- One investment/deployment serves multiple domains, does not re-invent the wheel. Lowers Capex
- No need to maintain domain-specific platforms, reduction in Capex
- Cross-domain service/application innovation with a common framework and uniform APIs, allows for sharing of information and processes across domains that were isolated thus far (e.g. home security system versus heating system), Supports new business opportunities.
- Re-use of the code whatever the domain was. Increases reusability / lowers Capex
- Data sharing and semantic interoperability brings the real value.
- Data oriented RESTful API design.
- Semantic data annotation, discover and reasoning facilitates intelligent analytics and service mashups.
- Security protection at both channel and object level, with static and dynamic access control.
- Open standards to avoid lock-in to a platform or a cloud provider.
- No single party or company controls the technology / features.
- Several open source implementations available (CSE or AE).
- oneM2M is an international standard
- Developed using standardization methodology that has insured successful interoperability in many technical domains, using the same process as in 3GPP.
- Developed by many companies based on consensus: it does not depend on a single or a small number of companies; not using a closed proprietary technology.
- It is an open standard: transparent development process & open access to all deliverables; all the specifications, even the drafts are available at http://www.onem2m.org/technical/latest-drafts
| In summary
The oneM2M initiative can remove fragmentation of the IoT world. Because it is independent of the access or protocol technology that is used for transport, it is designed to be a long term solution for IoT deployment. |
|---|
Functional Architecture
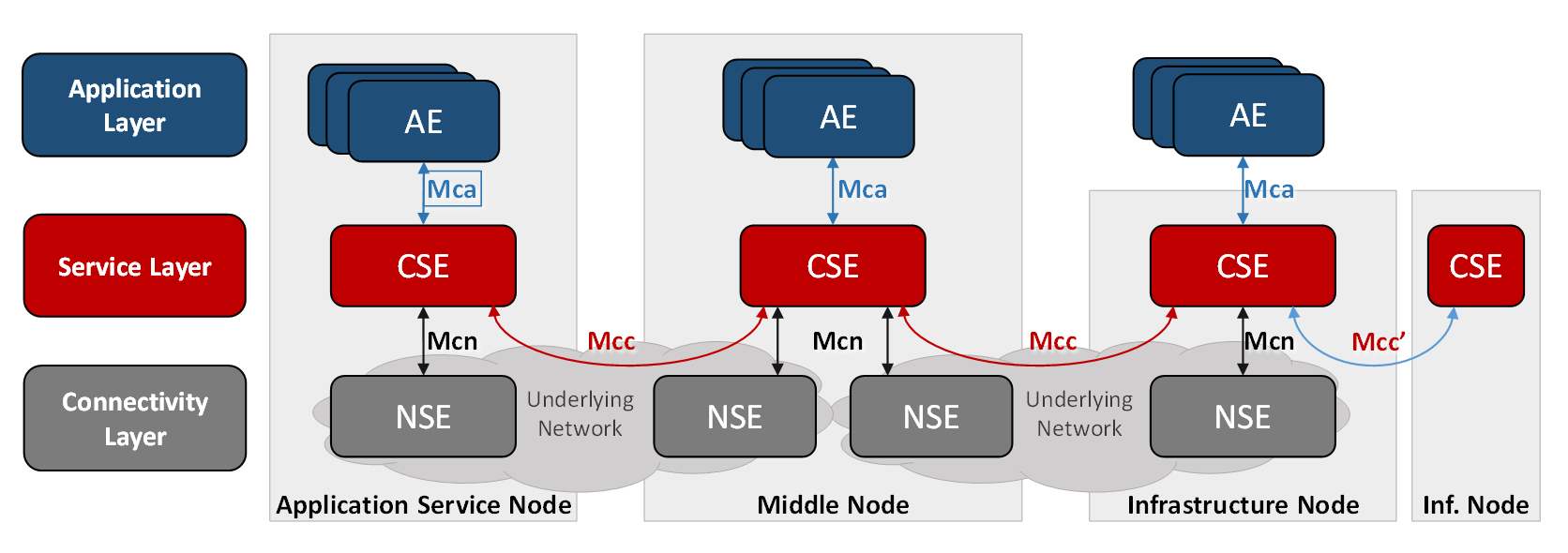
The oneM2M functional architecture comprises the following functions:
- Application Entity (AE): The Application Entity is an entity in the application layer that implements an M2M application service logic. Examples of the AEs include an instance of a fleet tracking application, a remote blood sugar measuring application, a power metering application or a pump controlling application.
- Common Services Entity (CSE): A Common Services Entity represents an instantiation of a set of "common service functions" of the oneM2M Service Layer. Examples of service functions offered by the CSE include: data storage & sharing with access control and authorization, event detection and notification, group communication, scheduling of data exchanges, device management, and location services.
- Underlying Network Services Entity (NSE): A Network Services Entity provides services from the underlying network to the CSEs. Examples of such services include location services, device triggering, certain sleep modes like PSM in 3GPP based networks or long sleep cycles.
To go further
More details of the achitecture and overview of the main functionalities and features could be found in the oneM2M site in the section Getting started with oneM2M “ <references />